Technology
Tomorrow's technology for today's world
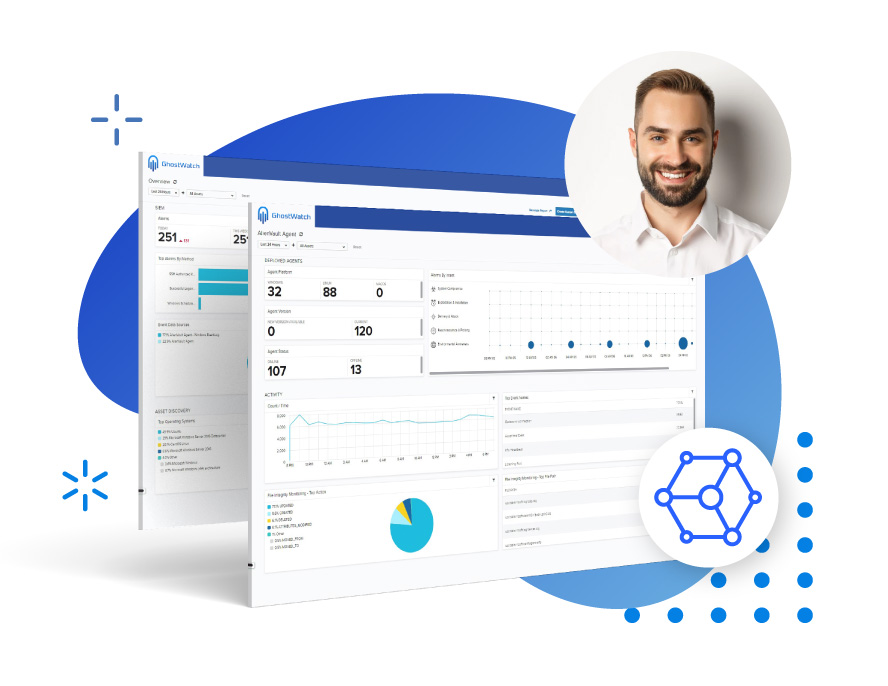
GhostWatch analyzes and detects vulnerabilities in critical assets and assigns a risk factor to each vulnerability corresponding with the Common Vulnerability Scoring System.
Cloud and On-premises
GhostWatch supports public cloud deployments including AWS, Microsoft Azure, and Google Cloud.
On-premises infrastructure is supported through GhostWatch’s integrated hardware appliances.

Amazon Web Services
• AWS API asset discovery
• CloudTrail monitoring and alerting
• Amazon S3 access log monitoring and alerting
• ELB access log monitoring and alerting
• AWS infrastructure assessment
• NIDS packet inspection

Microsoft Azure
• Azure API asset discovery
• Azure REST API monitoring and alerting
• Azure infrastructure assessment
• Azure security alerts
• Azure Microsoft Windows log locations

Google Cloud Platform
• GCP API asset discovery
• Cloud Pub/Sub monitoring and alerting
• Audit logs
• Stackdriver audit logs
Security Monitoring
The GhostWatch dashboard provides complete visibility of threats, incidents, response, and compliance management.
Threat Management
Our platform synchronizes threat detection, incident response, and threat management for rapid remediation
Advanced Endpoint
Threat Detection
Intrusion Detection
Threat Analysis
Ransomware Detection
Advanced Endpoint
Threat Prevention
Advanced Remediation
Management
Vulnerability Management
GhostWatch detects vulnerabilities in critical assets and assigns a risk factor to each vulnerability corresponding with the Common Vulnerability Scoring System
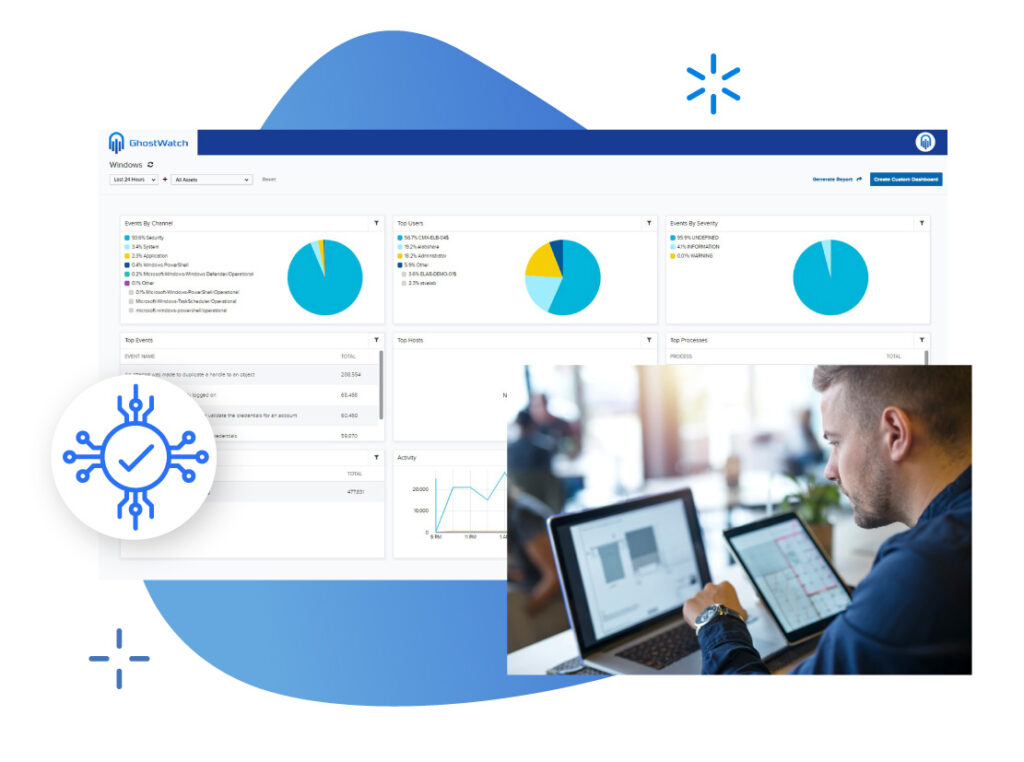
Vulnerability assessment and remediation
Continuously identify insecure configurations, unpatched, and unsupported software.
On-demand and scheduled scanning and reporting
Vulnerability scanning with actionable information
Context for security incident response
Vulnerability scanning
A simplified and more manageable network vulnerability scanner. GhostWatch stays ahead of attackers with advanced features.
Simple configuration and scheduling
Intuitive dashboard and reporting
Regular updates
Threat Intelligence
Connected to a global community of threat researchers and security professionals

Threat Intelligence
GhostWatch detects the latest global threats and prioritizes responses
Data Exfiltration Detection
Prevents leakage of sensitive and proprietary data
Real-Time Botnet Detection
Identify infection, compromise, and misuse of assets
Command-and-Control Traffic Identification
Identify compromised systems communicating with malicious hackers
IP, URL, and Domain Reputation Data
Prioritize response efforts by identifying known bad actors and infected sites
APT (Advanced Persistent Threat) Detection
Detect targeted attacks often missed by other defenses
Dynamic Incident Response and Investigation
Specific directives to respond to each alert
Network Security
Complete network security monitoring and intrusion detection.
To secure your network, first we need to know what to protect. GhostWatch will discover, inventory, and start monitoring your network in minutes.
Built-in asset discovery tools:
- Identify what’s on your network at any given time
- Understand how your devices are configured
- Correlate asset info with threat and vulnerability data
- Accelerate investigations of impacted assets
Polymorphic malware and zero day exploits often bypass preventative security measures. Context is critical so GhostWatch dives deep and continuously gathers data to understand “normal” system and network activity.
Behavioral monitoring capabilities include:
- Service and Infrastructure Monitoring
- NetFlow Analysis
- Network Protocol Analysis / Packet Capture
Log Management
GhostWatch performs advanced log analysis to provide actionable intelligence and threat alerts.
Event Correlation
- ● Integrated SIEM functionality
- ● Multisource log data correlations
- ● Threat intelligence updates
Log Analysis
- ● Fast, accurate forensic threat analysis
- ● Hundreds of ready-to-go plugins
- ● No fee custom plugins
Multifunctional Reporting
- ● Raw log visibility
- ● Tamper proof log storage
- ● Custom reporting engine